Water management
Measuring critical water infrastructure changes using LP-WAN technology.
IoT, or the ‘Internet of Things’, is currently the buzzword in the entrepreneurial world. Not bad. Thanks to this smart technology, devices connected to the same network can communicate with each other.
And that produces data. Lots of dates. Data that helps you optimize your business processes, develop new business models and do business sustainably. But all that data must be properly secured. Especially if you work in the security sector. To ensure this, ADI Global Distribution has entered into a partnership with IoT Unlimited and T-Mobile Ondernemen.
T-Mobile Ondernemen has been the connectivity partner for businesses in the Netherlands for years. We do not do this alone, but in collaboration with strategic partners such as IoT Unlimited. We have been working with this party for more than 5 years. This collaboration was recently expanded with a partnership with ADI Global Distribution. One of the largest distributors of security products in the world.
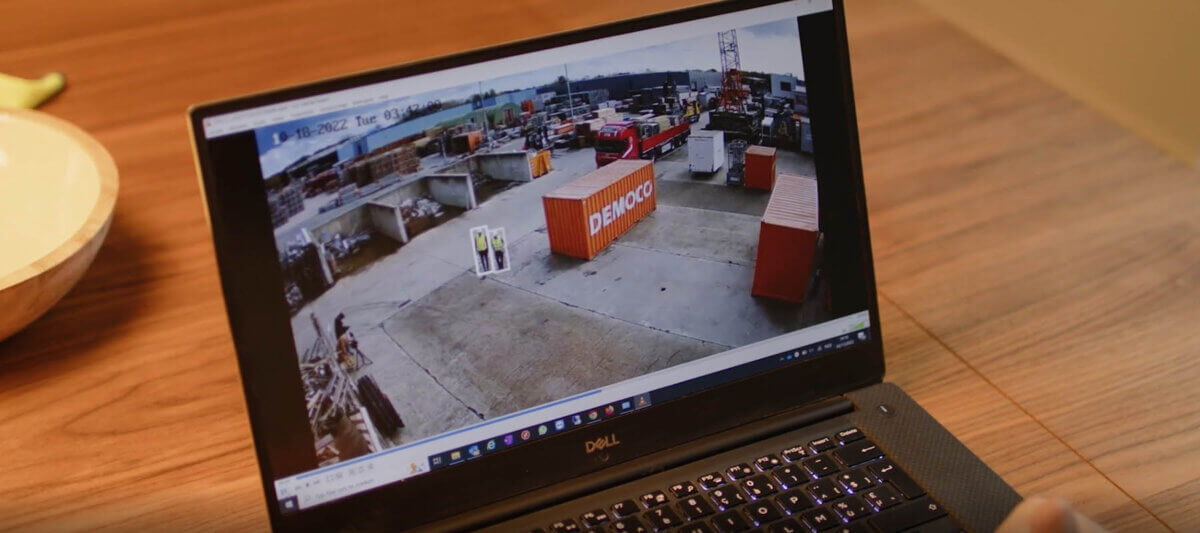
Connectivity has become increasingly important in recent years, including in the security sector. Koen de Rooij, General Manager Benelux ADI Global: “There was a huge need among our partners and the security installer to be able to integrate their solutions into a platform in a safe and flexible way.”
Floris van Amerongen, director of IoT Unlimited: “T-Mobile and ADI wanted to work together to offer smart and secure connectivity services to ADI’s partners. Both T-Mobile and ADI have a strong partner strategy and IoT Unlimited has made this possible as an enabler with its flexible distribution and security platform, acting as a bridge between the two major parties (MICK as a service). We help companies meet their IoT needs with a network-independent platform that incorporates existing networks and SIM cards. This way we can realize growth in a beautiful, but above all safe way for our customers. In our partnership with ADI, we are stepping into security industry security.”
Floris: “In principle, SIM cards are often used in the security world as back-up solutions for stand-alone projects. For example, with alarm systems to guarantee a connection to the control room via 4G or 5G. But it is also possible for IP cameras that are used to secure remote places where there is no internet (yet), such as construction sites. A third application is the use of SIM cards in personal security, in mobile emergency buttons.”
T-Mobile supplies the SIM cards and connects them to the IoT Unlimited connectivity platforms. Floris explains: “This platform makes it easier for installers to activate, manage and monitor services remotely. Users can log in at different levels with different rights and the installer can grant access to partners and even end users. An additional advantage of our independent platform is that we are able to integrate already delivered systems (read: SIM cards) from other suppliers into one platform. This gives our partner the advantage that we can work with all additional functionalities within a management environment.”
Floris: “A very important one. What you often see with IoT is that some ‘dumber’ devices are used in the field: devices that cannot connect to the internet. It is precisely then that you want to be sure that the security is in order, so that the data traffic, the communication between the devices, cannot be manipulated or influenced. Via our SAM platform (Secure Access Management platform), we ensure that traffic from the source arrives safely at your company network.
In addition, we are able to determine, in consultation with the ADI partner, what is or is not possible with a SIM card in order to prevent misuse. An important trend we are seeing now relates to remote access to systems. There is a shortage of personnel in almost all technical branches. With our SAM platform, we enable partners to access their systems remotely. In some cases, this prevents a trip to a customer location, something that is very valuable nowadays. With this solution, we are also building an independent solution from the hardware supplier, so that the partner has access to all systems in the field via a single platform/solution.”

Construction site security is a good example of IoT in the security industry. There are many cameras on construction sites that allow you to monitor the safety of the construction site. All these cameras send large amounts of data to a central, secure platform. You need stable and reliable connectivity to receive and process that data. And flexible partners who can switch quickly and who can offer the right solutions at the right times at different locations. Because nothing is as changeable as a construction site.
Would you like to know more about the partnership of IoT Unlimited together with T-Mobile Ondernemen and ADI Global Distribution and see a practical example of construction site security? Then watch the IoT reference video at the top of this article.
Different layers available for the international distributor and their partners.
Extensive reporting of revenue seggregated per partner and period.
Enabling the partner to remotely access their solutions.
Contact us for an introduction call
Need more proof?
Measuring critical water infrastructure changes using LP-WAN technology.
Our SAM-platform makes sure your data is securely processed to your network.
Redundant mobile network solution for the highest availability of services.
Cases that thrive of the added value of our scalable platform.
Backup services to ensure your business.
Our eUICC compliant sim cards are offered independently from any mobile operator.
Financial devices with specific connectivity requirements across Europe.